The Reality About Deepseek In 8 Little Words
페이지 정보
작성자 Kattie 작성일25-03-05 10:32 조회8회 댓글0건관련링크
본문
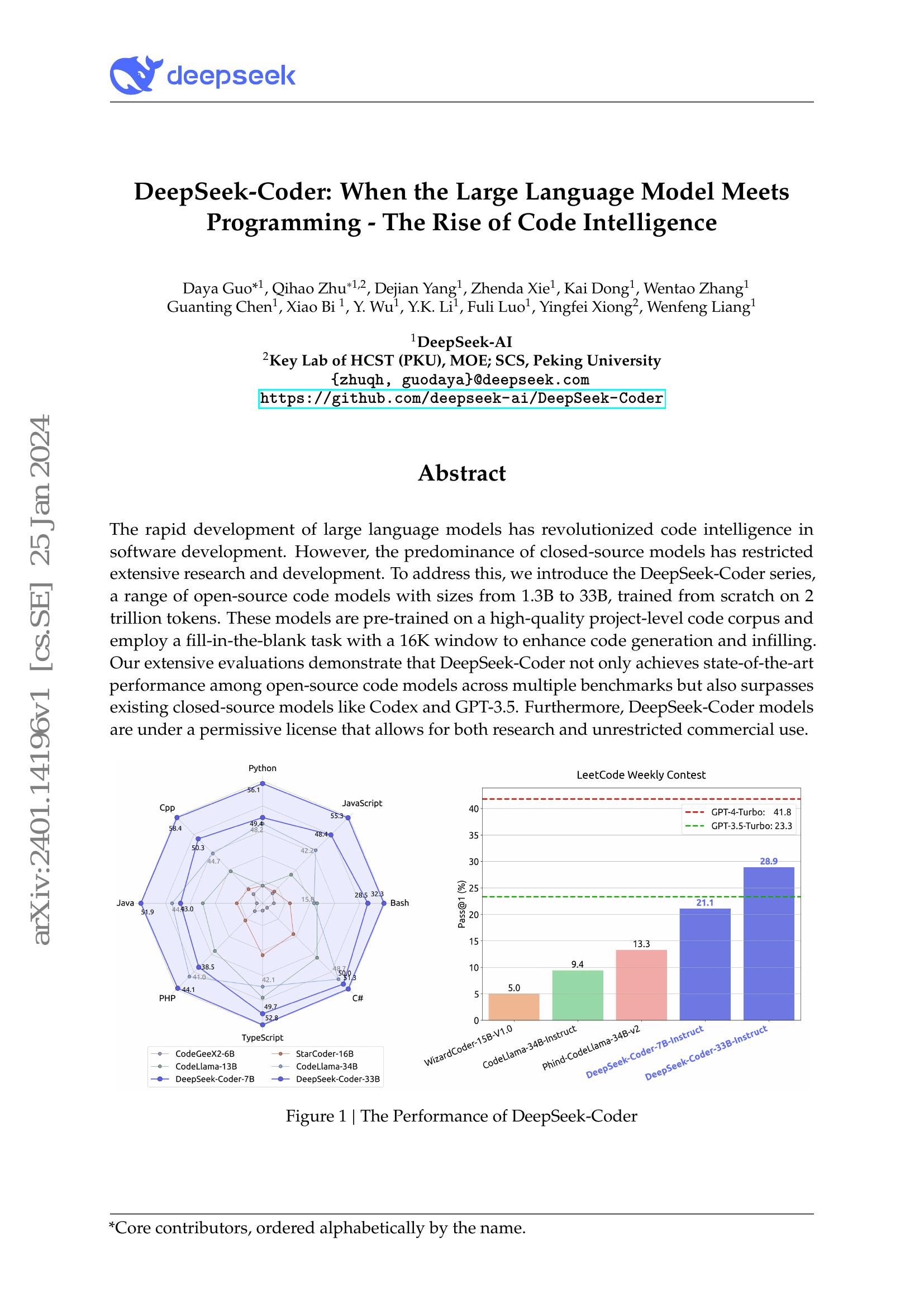 Results reveal DeepSeek LLM’s supremacy over LLaMA-2, GPT-3.5, and Claude-2 in numerous metrics, showcasing its prowess in English and Chinese languages. OpenAI and Microsoft are investigating whether the Chinese rival used OpenAI’s API to combine OpenAI’s AI models into DeepSeek Chat’s own models, based on Bloomberg. These distilled models, together with the main R1, have been open-sourced and can be found on Hugging Face under an MIT license. Generative AI fashions, like every technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can enable malicious actors to conduct attacks in opposition to them. Another set of winners are the massive client tech companies. Consequently, most Chinese firms have targeted on downstream purposes moderately than constructing their very own models. Now that a Chinese startup has captured a lot of the AI buzz, what happens subsequent? After which, someplace in there, there’s a story about know-how: about how a startup managed to construct cheaper, extra efficient AI fashions with few of the capital and technological benefits its competitors have. But with its newest launch, DeepSeek proves that there’s another method to win: by revamping the foundational construction of AI fashions and using restricted resources extra efficiently.
Results reveal DeepSeek LLM’s supremacy over LLaMA-2, GPT-3.5, and Claude-2 in numerous metrics, showcasing its prowess in English and Chinese languages. OpenAI and Microsoft are investigating whether the Chinese rival used OpenAI’s API to combine OpenAI’s AI models into DeepSeek Chat’s own models, based on Bloomberg. These distilled models, together with the main R1, have been open-sourced and can be found on Hugging Face under an MIT license. Generative AI fashions, like every technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can enable malicious actors to conduct attacks in opposition to them. Another set of winners are the massive client tech companies. Consequently, most Chinese firms have targeted on downstream purposes moderately than constructing their very own models. Now that a Chinese startup has captured a lot of the AI buzz, what happens subsequent? After which, someplace in there, there’s a story about know-how: about how a startup managed to construct cheaper, extra efficient AI fashions with few of the capital and technological benefits its competitors have. But with its newest launch, DeepSeek proves that there’s another method to win: by revamping the foundational construction of AI fashions and using restricted resources extra efficiently.
 That's about 10 times lower than the tech large Meta spent building its latest A.I. US tech corporations have been extensively assumed to have a important edge in AI, not least due to their huge size, which allows them to attract high talent from all over the world and invest huge sums in building knowledge centres and purchasing massive quantities of pricey high-finish chips. Nevertheless, this data appears to be false, as DeepSeek doesn't have access to OpenAI’s internal information and cannot present dependable insights concerning employee performance. Core components of NSA: • Dynamic hierarchical sparse strategy • Coarse-grained token compression • Fine-grained token selection
That's about 10 times lower than the tech large Meta spent building its latest A.I. US tech corporations have been extensively assumed to have a important edge in AI, not least due to their huge size, which allows them to attract high talent from all over the world and invest huge sums in building knowledge centres and purchasing massive quantities of pricey high-finish chips. Nevertheless, this data appears to be false, as DeepSeek doesn't have access to OpenAI’s internal information and cannot present dependable insights concerning employee performance. Core components of NSA: • Dynamic hierarchical sparse strategy • Coarse-grained token compression • Fine-grained token selection
댓글목록
등록된 댓글이 없습니다.